Network and Information Security Management

This module introduces students to the underpinning concepts of Computer Networks and the skills of Information Security Management. This includes an introduction to network security fundamentals and information security governance principles. It will be based on mapping information security management roles onto a number of security models. The module describes the security management and protection issues involving business resources, risks, monitoring as well as business continuity strategies. It will also discuss common diagnostic and monitoring tools utilised as part of a Network and Information Security practice such as nessus, snort, syslog and ELK. Students will be introduced to the techniques in an engaging format, using a mixture of group work and individual activities.
This module aims to:
Provide students with:
- An understanding of the fundamentals of computer networks and security
- An understanding of the principles of information security management
- An understanding of the use and benefits of various monitoring and logging tools
- An understanding of how to create and use security vulnerability and assessment tools, including relevant programming techniques
- An understanding of future network architectures and information security management
- The opportunity to reflect on and evaluate their personal development
- The ability to present critical arguments for specific actions or outcomes to a diverse audience
Collaborative Discussion 1
Upon reading Read Glisson, W., Andel, T., McDonald, T., Jacobs, M., Campbell, M. Mayr, J. (2015) Compromising a Medical Mannequin. Healthcare Information Systems and Technology (Sighealth). Answer the following discussion questions:
- What are the major threats and vulnerabilities discussed in the paper?
- How would you mitigate against these?
Initial Post
From evaluating the article "Compromising a medical mannequin" (Glisson, et al., 2015) it’s clear that the pace at which technology is moving forward in the medical industry is faster than the cyber security considerations are being evaluated. The particularly important observation that a breach of a training tool would result in a clinician receiving the incorrect guidance when problem solving is insightful. The discrepancy in technology to security considerations in this industry can potentially result in loss of life so should be treated with an urgency befitting that status.
Two types of attack highlighted in this paper were Denial of Service (DoS) attacks and Brute Force attacks. It’s important to mention at this stage that both types of attack are easy to perform with readily available software so, as such, should be taken very seriously.
Focusing initially on Brute Force attacks, the basic protection against it is easily implemented but by no means an exhaustive style of protection. According to the paper "Password Strength: An Empirical Analysis” (Dell’Amico, et al., 2010) the findings showed ability to brute force a password is reduced as the possible data set the password can be taken from is increased. This leads to the obvious implementation of a ‘minimal specification’ for a password securing an access point. A dictionary word being the lowest form of security up to a random string of characters being the highest. Increasing the number of characters increases the security by a significant factor with each character added. Despite this evidence it is well documented (Farik & Ali, 2015) that access point manufactures don’t employ this sort of security regularly. Designing the system with a simple “three strikes” rule for guessing access codes would halt brute force attempts quite quickly. When the code is guessed incorrectly a certain number of times the system should lock and not allow any more access attempts to be made. It has the added benefit of alerting a legitimate user of a current malicious access attempt because their access session would be locked out too.
DoS attacks are a popular and complex problem in current cyber security due to the ever-expanding complexity of attacks and intelligence of the server requests. Two papers (Prakash, et al., 2016), (Kumar & Amin, 2021) detail ways that current technologies can be leveraged to qualify the type and purpose of connections to a server to catch malicious connections. Requests not meeting the requirements for a legitimate connection are discarded keeping server load to a minimum. The battle with this sort of attack is the increasing complexity with which these requests are made. As quickly as a new exploit is patched, malicious hackers find new ways around the systems. The current trend of utilising blockchain technologies allows for security solutions to evolve automatically, to a degree, which will help to keep up with the attackers, but is by no means a silver bullet.
However, utilising experience from a background in chemical laboratory management, applying the principle of parsimony “entities should not be multiplied beyond necessity” or, to paraphrase, the simplest explanation is usually the best one. The first solution that should be applied to this specific situation is to analyse if a wireless connection from the medical mannequin is even required in the first instance. A physical connection between mannequin and controlling devices would eliminate a remote attack. A physical cage for storage of controlling machines would eliminate malicious control of the software. While comparatively “low tech” these solutions should be the first consideration when deploying these devices. Firstly, ask yourself “Do we have to use this specific setup” before exploring ways to mitigate issues with a system we might not have to use.
References
Dell’Amico, M., Michiardi, P. & Roudier, Y., (2010). Password Strength: An Empirical Analysis. s.l., s.n.
Farik, M. & Ali, A., (2015). Analysis Of Default Passwords In Routers Against Brute-Force Attack. International Journal of Scientific & Technology Research, 4(9).
Glisson, W. B. et al., (2015). Compromising a Medical Mannequin, s.l.: s.n.
Kumar, S. & Amin, R., (2021). Mitigating distributed denial of service attack: Blockchainand software-defined networking based approach, networkmodel with future research challenges, s.l.: Wiley.
Prakash, A., Murali, S., Bhargav, T. S. S. & Natarajan, B., (2016). Detection and Mitigation of Denial of Service Attacks Using Stratified Architecture. Procedia Computer Science, Volume 87, pp. 275-280.
Summary Post
Based on the responses from my peers, strides are being made in consideration of cyber security in the medical industry. It’s very apparent though that a lot more ground needs to be covered and more in-depth analysis needs to take place.
In my initial post I laid out the idea of a “three strikes” system to lock out repeated attempts to log into the system. It was highlighted by Beran Necat the importance of multi-factor authentication (Necat, 2021) within this idea, and the importance of speed of access by Austin Mundy (Mundy, 2021). When deployed thoughtfully and efficiently it can be implemented adding only a small amount of time to individual logins. The presence of MFA in a login procedure will not only increase the security of that process but also act as a deterrent to hackers. The system, depending on how valuable the target is perceived, could be deemed to be not worth the effort of cracking the security (Soni, 2021). With the huge virtual landscape of websites and servers, a hacker will always be able to find an easier target.
As a proposal to mitigate down time brought on by Denial-of-Service attacks (DoS), Edward Van Biljon suggested the concept of a hot site (Van Biljon, 2021). While a hot site could be of some assistance in instances like this it would first have to be carefully considered exactly what hardware would be getting replicated. While there is worth in duplicating training equipment in an off-site location, copying clinical hardware wouldn’t carry much benefit. In the clinical environment, if the systems are brought down by an attack, it wouldn’t be possible to migrate to the hot site location as the patients that would be being cared for cannot move. Duplicating patient databases might carry some worth, but the access systems local to the patients go down it wouldn’t help to have hardware duplicated elsewhere.
References
Mundy, A. (2021, November 29). Collaborative Learning Discussion 1. Retrieved from University of Essex Online - The Virtual Learning Environment: https://www.my-course.co.uk/mod/hsuforum/discuss.php?d=285456
Necat, B. (2021, November 29). Collaborative Learning Discussion 1. Retrieved from University of Essex Online - The Virtual Learning Environment: https://www.my-course.co.uk/mod/hsuforum/discuss.php?d=285456
Soni, R. (2021, February 12). 3 reasons why customer-focused enterprises should trust MFA. Retrieved from Security Info Watch: https://www.securityinfowatch.com/cybersecurity/information-security/managed-network-security/article/21210089/3-reasons-why-customerfocused-enterprises-should-trust-mfa
Van Biljon, E. (2021, November 29). Collaborative Learning Discussion 1. Retrieved from University of Essex - The Virtual Learning Environment: https://www.my-course.co.uk/mod/hsuforum/discuss.php?d=285456
Collaborative Discussion 2
Initial Post
Group 2 were assigned allmytype.co.uk to investigate and analyse for security vulnerabilities.
The first tool used was the Trace Route tool built into Windows (Gerend, et al., 2021) to track the route from my laptop to the webserver hosting the site. The tool revealed 13 hops from my laptop to the site with an average delay at each hop of about 46ms, as can be seen in Figure 1.
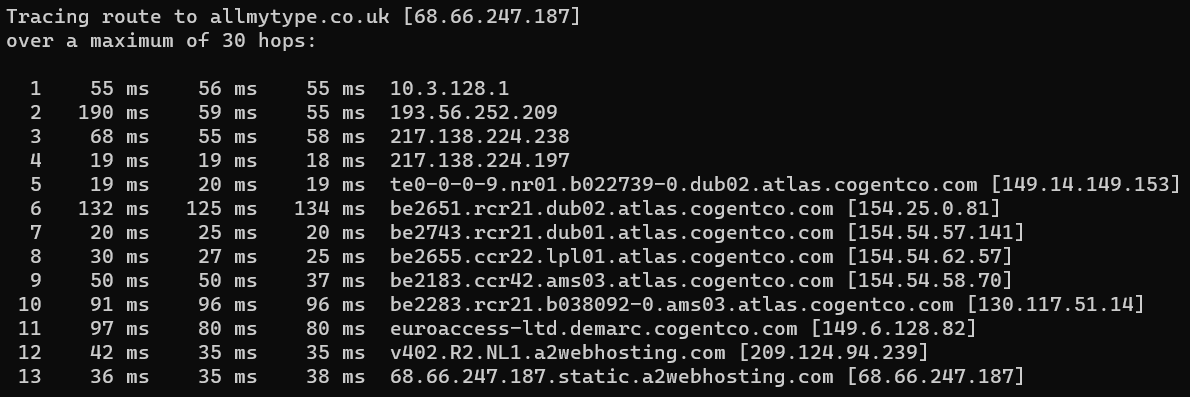
The biggest delay is caused at hop 6 as the route goes through servers hosted by the ISP Cogentco.
Using the tools from DNSChecker (DNSChecker, 2021) the main nameserver records (NS) are revealed to be ns1.a2hosting.com, ns2.a2hosting.com, ns3.a2hosting.com and ns4.a2hosting.com. Using the same investigation tools the MX record is revealed to be mail.allmytype.co.uk. The registrar of the domain is Enom LLC (enom.com), a domain reseller, whose details are redacted for privacy in the WHOIS database. Using the hosting checker tool by Hosting Checker (Hosting Checker, 2021) it’s revealed the page is hosted by A2hosting.com in the Netherlands. A note on A2 Hosting though is that they are based, and have their site hosted, in Ann Arbour, Michigan, USA. The Dutch data centre obviously being a location they utilise for their European customers.
References
DNSChecker, 2021. DNSChecker. [Online]Available at: https://dnschecker.org/[Accessed 20 December 2021].
Gerend, J. et al., 2021. Microsoft Docs. [Online] Available at: https://docs.microsoft.com/en-us/windows-server/administration/windows-commands/tracert [Accessed 19 December 2021].
Hosting Checker, 2021. Hosting Checker. [Online] Available at: https://hostingchecker.com/ [Accessed 20 December 2021].
Reflective Piece
Unit 1
In this unit I was introduced to the very basics of Information Security Management. We touched on the things that constitute a threat and a vulnerability and looked at a handful of roles within the industry. I wrote the initial post for the first collaborative discussion and in my research it was interesting to explore the way a medical training device could compromised. I enjoyed learning about the computing side but also about the medical processes needed. We also had our teams assigned for the rest of the group work so I set up a Teams group where we could chat. At the time I thought it was going to be interesting to see how the team would work spread across different time zones. I thought that the group work would struggle as cohesive conversation would be a challenge. The Teams group proved to be a neat solution for the problem as it enabled us to have a central location for text chat that would be archived, and with the integration with Office365, a central repository for live documents.
Unit 2
In this unit I attended the STRIDE & DREAD tools seminar. I prepared for it by going over what the STRIDE & DREAD stood for and some examples of their use. As this isn’t my current field of expertise I hadn’t come across these before so it was interesting to read about. I was concerned that this sort of topic, with my lack of knowledge on the subject, would hinder me in my understanding. However, it was interesting to learn about the security focuses of my peers, especially as they already work in this sector. It’s helped to see how the sector currently operates and what current trends are.
Unit 3
In this unit we finished off our collaborative discussion around the medical mannequin. It was good to get feedback on my initial thoughts from Beran, the module leader, about how to further secure the mannequin and from Austin, my peer, on the importance of ease of access despite security layers. That helped me see how my ideas might be perceived in the real world since my work is purely theoretical. Austin currently works in the sector so his input gave me important points to consider. We also started the design document to be submitted in unit 6. I had some input into the formatting of what had already been written as the team were getting citations wrong.
Unit 4
This unit was interesting to me as it was the start of some practical skills in penetration testing and hunting for vulnerabilities. This is something I haven’t done before so I found this quite enjoyable and very informative. This unit also included a seminar session that I was unable to attend as now they fall within work hours and I cannot take that time to be involved. I was initially worried this would impact my learning but I found the recordings of the sessions easier than expected to follow and use as a tool for catching up.
Unit 5
This was a unit I was more comfortable with as it’s centred around technologies I’ve utilised myself and implemented on my own personal networks. I felt more confident in discussions involving these technologies. It was interesting to learn about the virtualisation of the hardware I own (router, switches) when considering cloud based networks though. It was great to learn about these aspects as this is the direction the sector is clearly heading in. As a group we went over our final draft for the design document. The team had worked very well despite the difficulties with time zones.
Unit 6
This unit went over some common tools within the sector that would be used by the engineers. This is something that I had long wondered about but had no access to. I was surprised to learn about how readily available these tools are but it will take a lot of practise to truly make use of them. The final design document was also submitted and we were all very happy with the quality. This was also a chance for me to submit a peer evaluation document. I spent some time considering all my peers and their influence on the project and on each other. Overall the team work has been a positive experience. I also had the chance to sit and reflect formally on my contributions so far. Despite my own struggles I feel I’ve made a positive impact although my initiative taking could be improved.
Unit 7
This unit introduced me to Kali Linux. I’d never heard of this system before and couldn’t believe how comprehensive and powerful it was. I spent some time working with the system to try to evaluate the website we had been assigned as a group but struggled to make meaningful sense of the results. Through discussion with the group, some who already worked in the sector, I started to understand the results I was getting. More work with this is clearly required though, it will take a while to master.
Unit 8
In this unit we looked at some real world examples of the application, and breaches, of GDPR. AS GDPR is something that has been introduced here in the UK, I was better placed to understand the process than some of the other group members that live in other parts of the world. I helped my team understand of the day to day implications as I have to be mindful of GDPR in my work. The others found it valuable.
Additional Documents
Professional Skills Matrix
Here is a link to my Person Skills Matrix highlighting my strengths and weaknesses within the skill set required in a Computing role.
Action Plan
Here is a link to my Action Plan that outlines how I intend to address shortcomings in my skill set and how I will measure my progress.
Team Notes
Here is a link to the team notes. The notes were a live document constructed throughout the module.